虎符决赛
虎符决赛
manager
nodejs的replace函数存在$匹配符,可绕过双引号过滤。
https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/String/replace#description
然后联合查询让查出来的密码和输入密码相等即可
1 | |
登录之后发现可疑的url,发现这是个应用Rocket.Chat,下载之后连接即可。需要在hosts文件中把secret-chat.manager.icq和题目ip绑定

注册登录之后发现写了一个robot,并且可以执行redis命令。利用恶意redis服务器打主从复制
1 | |
恶意服务脚本
1 | |
执行命令知州读取flag即可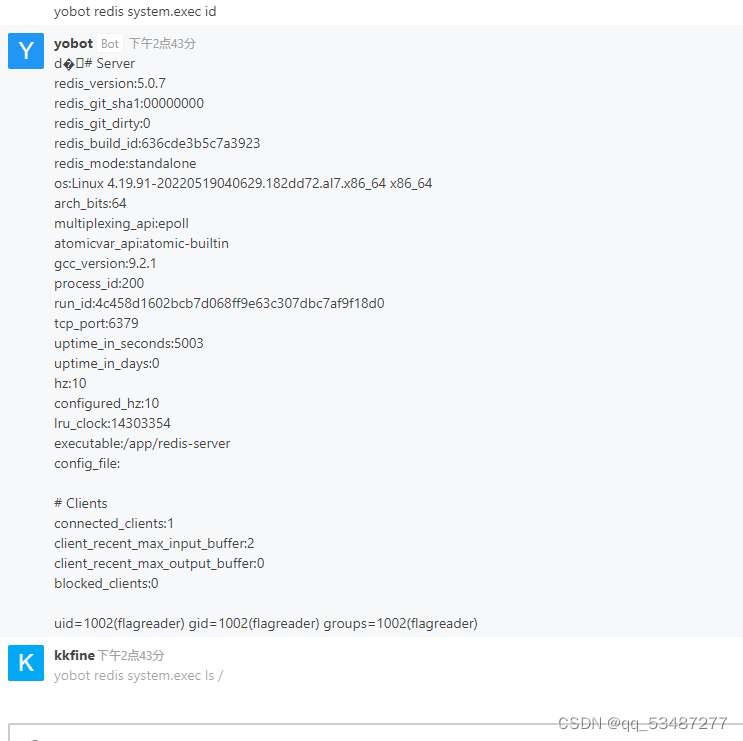
龙卷风
python的tornado框架ssti注入,但是黑名单几乎把可以利用的都ban了
1 | |
发现可以利用unicode进行绕过,但是点号引号不知道怎么绕过了。赛后学习到了可以用request请求中携带我们需要执行的命令,然后利用eval(repr(request)[x:x]来获取url中的命令字符串并用eval执行命令。
脚本如下,切片的长度需要本地给黑名单去了先调试一下。
1 | |

readygo
过滤了大小写字母,最后面存在 eval.Eval执行命令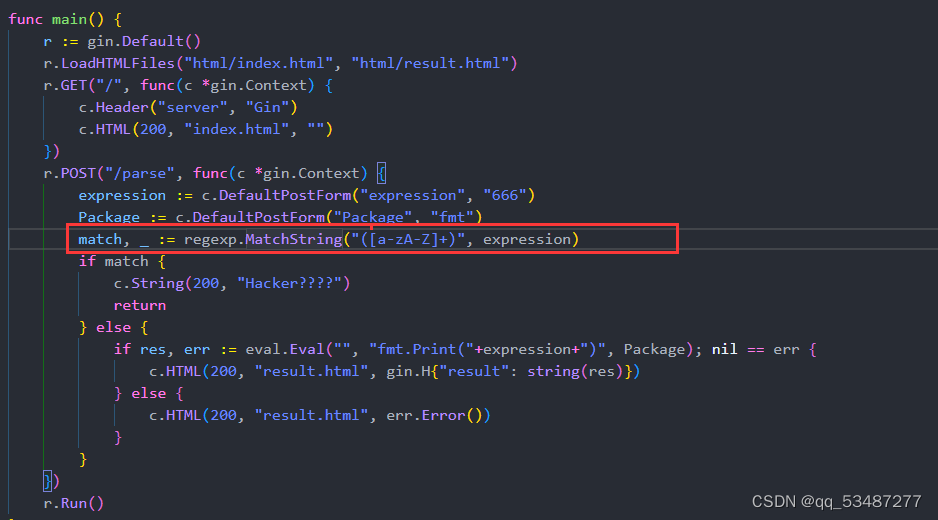
在 eval.go源码里面importStr并没有过滤限制,并且是进行的简单字符串拼接。所以我们可以将后面的func注释掉,自己写func函数然后执行命令。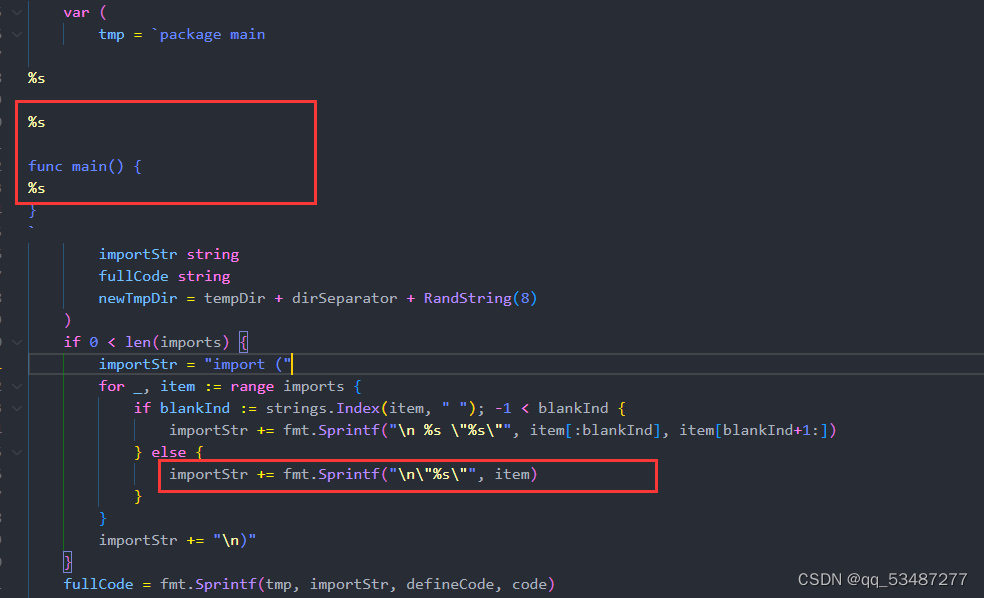
测试代码
1 | |
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!